Manage security settings for Windows Servers with Microsoft Endpoint Manager
A more thorough title for this post would be “Use Security Management for Microsoft Defender for Endpoint to deploy security configurations from Microsoft Endpoint Manager to Windows Servers.” But let’s be honest, that’s way too long of a title.
Let’s explain what we’re actually doing. Currently in public preview, Microsoft Defender for Endpoint (MDE) can integrate with Microsoft Endpoint Manager (MEM) to deploy security policies to devices that aren’t managed by MEM. MEM is acting as a portal/management console, but the device itself is communicating with MDE to consume policy. Cool, right?
From that Docs page, the following diagram explains the three different ways the MEM admin portal can be used to manage devices – Intune, ConfigMgr, and Defender for Endpoint.
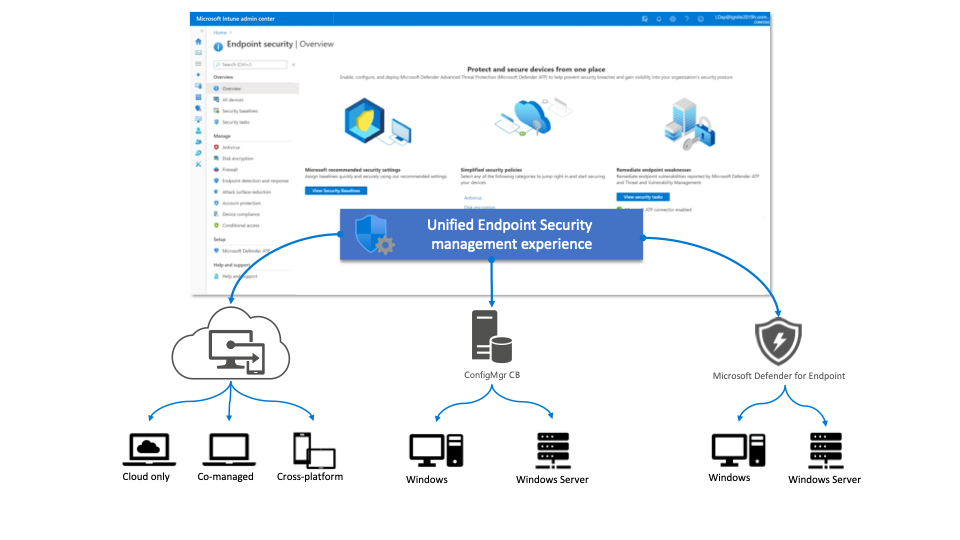
Really, the key scenario here is having some manageability over Windows Servers in your environment without needing to build out an entire ConfigMgr environment. Although – it’s still much preferred to use it if you can, considering how much more ConfigMgr can do. On that note – here are the currently supported workloads for MDE Security configuration:
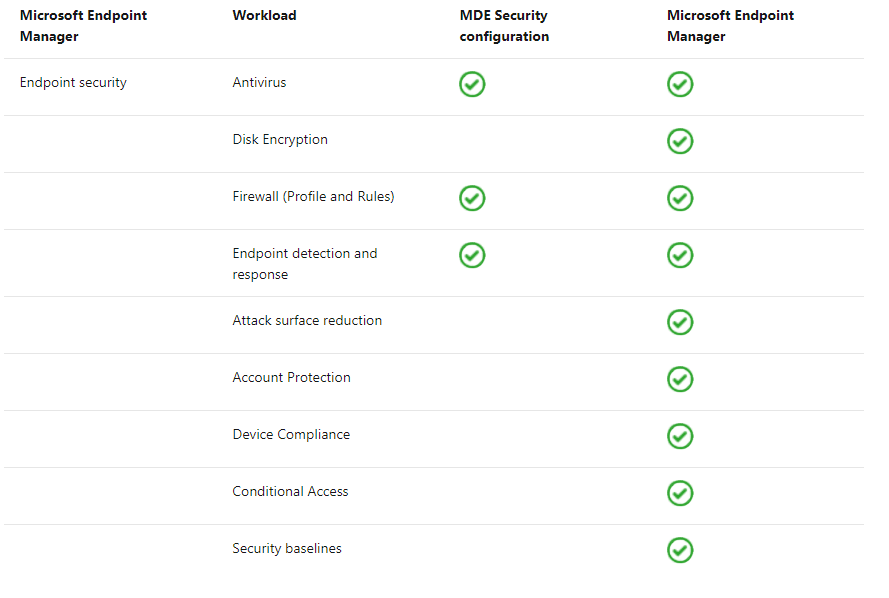
Pretty slim compared to the MEM workloads. But – if Firewall and Antivirus is mostly all we need, then it’s perfect! Let’s test it out.
Enable MDE Security Configuration Management
In my environment, I have licenses for MDE but have not enabled anything. In the MDE portal (security.microsoft.com), I’ll first need to enable preview features: Settings > Endpoints > Advanced features > Preview features > On

Then I’ll be able to go to Settings > Endpoints > Configuration management > Enforcement scope, where I can enable OS platforms for security setting management:

Then in the MEM Console (endpoint.microsoft.com), I’ll set Tenant administration > Connectors and tokens > Microsoft Defender for Endpoint > Allow Microsoft Defender for Endpoint to enforce Endpoint Security Configurations (Preview) > On

Perfect!
Onboard devices for MDE Security Configuration Management
There are 6 ways to onboard Windows devices into MDE:

The easiest for this purpose is Group Policy. We don’t want to use a local script, because that’s for testing. And using MEM/MECM kind of defeats the purpose, because then they will receive security configuration from those management platforms rather then MDE. VDI Scripts and MDfC would also work for this scenario, but since we have domain-joined devices, Group Policy is our easiest choice.
In the Microsoft 365 Defender portal, we’ll go to Settings > Endpoint > Device Management > Onboarding:

Then we’ll select our platform (in this case, I’ll be deploying to Windows Server 2019), and Group Policy under deployment method. After downloading the .zip file, I’ll extract into a location where my servers have read-only access (in this case, \\domaincontroller\SYSVOL):
Following the step-by-step instructions here, we’ll create a GPO with a scheduled task to onboard devices:




Now, on a server that is targeted by the Group Policy (in this case I’m using my ConfigMgr server, which is conveniently not being managed by CM), I’ll manually force an update for testing:
If I open Task Scheduler on the targeted server, I’ll see that the scheduled task is there as expected:

And after a few minutes, we’ll see that the device is onboarded into Defender for Endpoint!

On the device itself, one easy way to check the status is by verifying the registry key: HKLM\Software\Microsoft\Windows Advanced Threat Protection\Status\OnboardingState is set to 1

Now, notice that these devices haven’t shown up in MEM yet. That’s because we still need to tag devices with MDE-Management. This step is done after it’s onboarded, to enroll it into the Security Management feature. If we click into a device (security.microsoft.com > Device inventory > devicename), we can go to Manage tags to add it:
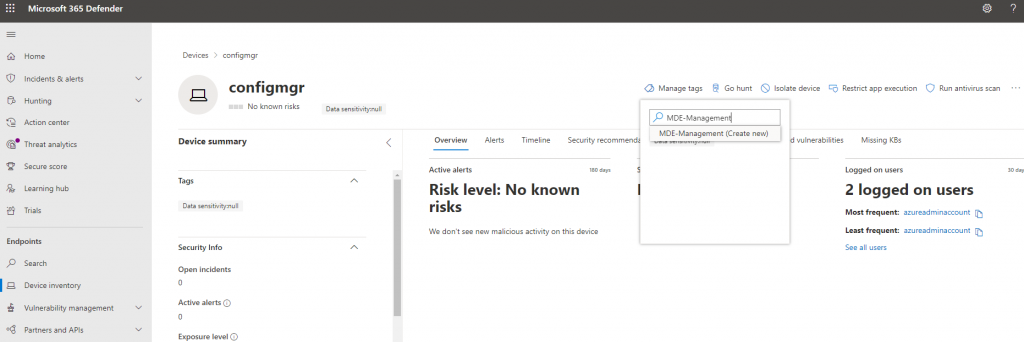
Then we’ll see our tagged devices with the tag listed in the Device inventory:

About 30 minutes later, the devices will be in Microsoft Endpoint Manager!

Deploy Security Policy
With our devices in MEM, deploying security policy is easy. First we’ll need a device group with our MDE Managed devices:


For the policy itself, we go to the Endpoint security node and select any of the following: Antivirus, Firewall, Firewall Rules, or Endpoint Detection and Response. We know that a policy is able to target MDE Managed devices because when we go to create it Windows Server (Preview) is listed:

The other available platforms handle different management planes. Windows 10 and later and macOS use Intune MDM to push policy. Windows 10, Windows 11 and Windows Server (ConfigMgr) uses tenant attach to target ConfigMgr managed devices. The Preview policy uses both Intune MDM managed devices and MDE managed devices, so be sure you are targeting the correct devices!
I’ll make a simple Antivirus profile. In the Endpoint Security node, click >Antivirus > + Create Policy > Windows 10, Windows 11, and Windows Server (Preview) > Microsoft Defender Antivirus

Provide a creative Name and click Next:

And then select some Defender settings to be applied to the device:

Target my MDE Managed Servers group:

And click Create!

Notice that the profile references using the microsoftSense to target devices (which is the MDE agent):

After a moment we’ll see that the profile applied as expected:


That’s all it takes to start using the new Security Management for MDE through MEM. If you’re using this feature, let me know the scenarios it fits with best! Until then, enjoy managing more device! 🛫







Janusz, thank you for the detailed information. This is very helpful. After following the above mentioned steps, I was able to get Windows Server 2019 to show on Intune. I’m now trying to remove the Windows Server 2019 from Intune, however I’m unable to remove\delete the device from Intune, as it gives a ‘Bad Request’ error. Intune support informed that this is due to the fact that the device is not managed by Intune, rather it’s managed by Microsoft Defender for Endpoint. Is there any option to remove the Windows Server from appearing on Intune portal?
In MDfE, you could turn off that Windows Server OS option for the endpoint security settings management. Basically turning off the option that synced them over in the first place. Would that work?