How to disable the “Your organization requires Windows Hello” prompt during OOBE
If you’re seeing the “Your organization requires Windows Hello” or “Use Windows Hello with your account” prompt during the out of box experience (OOBE), but thinking to yourself – “I never set up Windows Hello for my organization…” then you’ve come to the right blog post! We’ve covered how to set up Windows Hello for Business before, but maybe there is some reason you would like to disable the prompt for your organization.

Here’s the quick steps for disabling the prompt:
First, head to the Microsoft Endpoint Manager admin center and click Devices > Windows > Windows enrollment. You’ll need to be signed in with an Intune Administrator role.

Click Windows Hello for Business, then under Configure Windows Hello for Business, select Disabled.

Click save and that’s it! During OOBE, you’ll now skip the “Your organization requires Windows Hello” prompt automatically. Here’s a sped up gif showing how OOBE looks without the prompt:

Now, there are other locations you can edit the Hello for Business settings – like the Endpoint Security pane in MEM (using security baselines or configuration profiles), but the settings in the Windows Enrollment pane are the only ones that apply during OOBE. Unfortunately, these settings also apply to the entire tenant and can’t be scoped. So if you want to remove the Hello for Business prompt during OOBE (for Autopilot, for example), you would have to block it for everyone using the tenant wide setting.
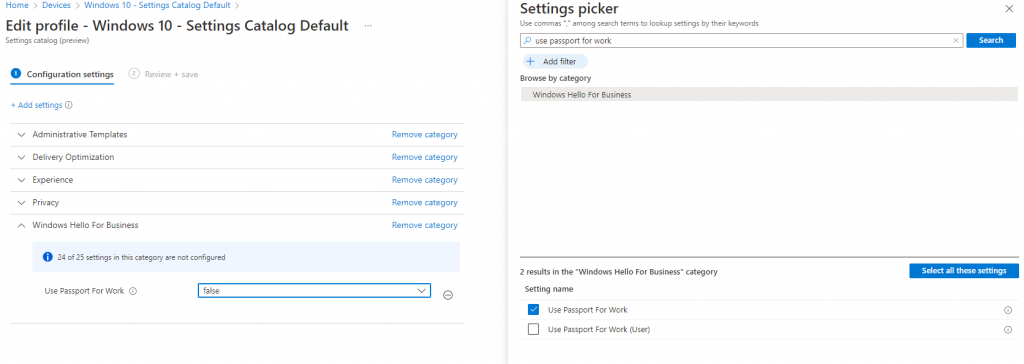
If you are still seeing the Hello for Business prompt after setting it to disabled in enrollment settings, try also configuring the following security catalog setting. Go to Devices > Configuration profiles + Create profile > Settings catalog (preview), or select an existing settings catalog profile. Click + Add settings, search for Use Passport For Work, and add the Use Passport for Work setting from the Windows Hello for Business to your settings catalog profile. Set Use Passport for Work to False, and deploy to a device group (so the setting processes before WHfB is provisioned on the device).
You may also be wondering why the prompt shows up at all when you haven’t set anything up before, it seems it’s because of Azure AD and Office 365. According to this docs article, for organizations that use Azure AD as part of O365: “When Windows 10 was released to general availability, Microsoft changed the behavior of the Office 365 Azure AD stack. When a user selects the option to join a work or school network, the device is automatically joined to the Office 365 tenant’s directory partition, a certificate is issued for the device, and it becomes eligible for Office 365 MDM if the tenant has subscribed to that feature.” This basically results in Hello for Business, which is default to enabled, automatically working and being “required” (although you could still skip it by pressing the X in the top right corner during OOBE).
Have any questions? Comment below! And as always, happy deploying! 🚀







Thank you! This has been driving me crazy!
Thank you!
This “hello” is super annoying during lockdown, when you want to pre-setup the devices for your new employees while they’re not sitting next to you and can’t register their fingerprints, face recognition or their smartphone.
Tried doing exactly this, and still get the prompt to setup Windows Hello! Any other pointers?
This is the one location for configuring the Windows Hello prompt during OOBE, and I’ve seen it take effect very quickly (within a few minutes). I would suggest testing with a licensed cloud-only Azure AD account in your tenant to make sure there’s not issues with the account itself (if you happen to be syncing accounts from on-prem, or using an un-licensed account). If that doesn’t work it might be best to open a ticket with Microsoft and have an engineer review the configuration.
Let us know if you end up finding the issue!
There is now another place you can disable Windows Hello using an Endpoint Security Policy of Type Account Protection, see link. I’ve successfully disabled this for autopilot, but doesn’t seem to disable it for user joined devices.
Hm, I actually tested the Endpoint Protection Account Protection settings too but was never able to disable the Windows Hello prompt. Tried via user-driven mode Autopilot, ESP enabled/disabled, and just a regular AADJ+MDM scenario. Can you tell me more about your test?
Hello,
Thanks for this post.
I do like windows hello and option not to enter password but its true that sometimes its annoying when it shows up for user who’s not sure what to do. ( we didn’t yet officially enable this solution only for pilot group)
My question is if i disable that option mention in the article will users able to enroll themself to WHfB?
What will happen with already whfb enrolled user?
Will this option remove wh auth provider?
There is a group policy setting “do not show wh enrollment on startup” (not remember exact word cause away from computer) and currently we skip this annoying whfb screen with this setting. We actually just create few registry keys and apply thru configuration profile. Its work like expected doesn’t bother user on login and for users who would like to use biometrics etc they just go to sign-in accounts and setup pin and then fingerprints.
Thanks,
Andrew
“Do not start Windows Hello provisioning after sign-in” option under “Administrative Templates / Windows Components / Windows Hello for Business / Use Windows Hello for Business”
Hello!
I have the same question: what happens to the existing users that have already created a PIN for Windows Hello when when switching “Configure Windows Hello for Business” to Disabled? Does their PIN get reset or stays unchanged? Does the PIN option dissapear and they are prompted to login with their AzureAD passsword?
Also, is there any way to find out which user have had PIN created?
Thank you!
Hi, I just tested this out and it looks like it’s affects the provisioning rather than the current configuration. Meaning, if a device already went through Hello for Business and then you disable the policy, it won’t revoke the Hello for Business log in on the device. if you’d like to disable Hello for Business, you can deploy a Identity Protection configuration policy set to Disable: https://docs.microsoft.com/en-us/mem/intune/protect/identity-protection-configure#create-the-device-profile
As for reporting – I haven’t found a way to see which users have created a PIN, unfortunately.
No option to supercede this policy with another one so that you can control who it applies to?
Any experiencing using ‘account protection’ policy as detailed here: https://docs.microsoft.com/en-gb/mem/intune/protect/endpoint-security-policy#create-an-endpoint-security-policy to create windows hello policy that applies only to a subset of users?
Unfortunately no, it seems like it’s everyone or no-one for the prompt during OOBE. I did test the account protection policy (mentioned in my previous comment) but could never get it to work. If you (or anyone reading this!) has gotten the account protection policy to disable the WHfB prompt let me know your scenario/settings, would definitely be an improvement to be able to target users.
We are getting the “Use Windows Hello with your account” during OOBE with Win 10 1909, but our organization doesn’t have Azure AD Premium. There seems to be no way to turn this off in the AzureAD admin as there is a “No Access” error when trying to get to Devices, Windows, Windows Enrollment in the Endpoint Manager as this page suggests.
Continuing through the setup with Hello, pops up the MFA login, even if it is not enabled/forced for the user, so really the Hello window doesn’t break anything. It is just annoying for the user.
Yeah I believe that’s correct – to disable the Hello prompt you need an Intune license to access the setting in the MEM portal.
I was able to rid of this annoyance by tweaking a registry setting on the device in audit mode (Ctrl-Shift-F3) before OOBE is run.
# Stop Windows Hello #
REG ADD “HKLM\SOFTWARE\Policies\Microsoft\PassportForWork” /v Enabled /t REG_DWORD /d 0 /f
Microsoft support confirmed there is NO WAY to do this in AzureAD without Premium.
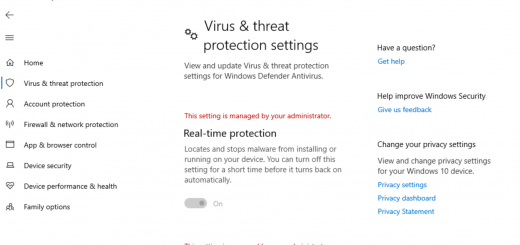
Hi, If we disable the prompt by setting Configure Windows Hello for Business: Disabled (Ref https://docs.microsoft.com/en-us/mem/intune/protect/identity-protection-configure#create-the-device-profile) , does it mean users CANNOT setup WHfB even using Sign-In Options –> Hello Fingerprint/Face/PIN ?
Correct – setting the identity protection device configuration profile to disabled will block WHfB from the settings pane. Here’s what it would look like for the end user: screenshot
I have not managed to disable Windows Hello. These are the steps I have tried.
1. endpoint.microsoft.com -> Home -> Devices -> Windows -> Windows Hello for Business -> Configure Windows Hello For Business: Disabled
2. endpoint.microsoft.com -> Home -> Endpoint security -> Account protection -> Create policy: Account protection (Preview) -> Block Windows Hello for Business: Enabled, Assigned for all users
3. endpoint.microsoft.com -> Home -> Devices -> Configuration profiles -> Profile: Indentity protection -> Configure Windows Hello For Business: Disabled, Assigned for all devices.
Now I press Autopilot reset for a laptop. Wait for Windows installation. Log in -> Windows Hello prompt is displayed. I don’t know that to try next.
What happens when you try a Wipe instead of Autopilot Reset?
I tried wiping and I selected ‘Wipe device, but keep enrollment state and associated user account’. I got the same Windows Hello prompts.
Did you ever get this? I’m in the same boat…disabled in windows enrollment, with a configuration profile, and an account protection policy thru endpoint manager. STILL GETTING WHfB prompt, sigh.
I have the same issue. User-Driven Autopilot settings. Wiped device. As soon as it is connected to a network in OOBE it goes through the user driven process. Everything works fine until after the user signs in and it prompts them to set up Windows Hello. If they click OK they get a prompt to enter more information for security asking for a phone number. MFA is not enabled for this user group and the users affected are students so we cannot have them with these restrictions.
I opened a support case with Microsoft but I am not optimistic they will be helpful.
No. We still have the same problem. We opened a support case with Microsoft on wednesday January 12, 2022.
Microsoft confirmed that at the moment you cannot disable Windows Hello from Intune. This is unexpected behaviour.
1. You can set GPO for image
“[Computer or User] > Administrative Templates > Windows Components > Windows Hello for Business > Use Windows Hello for Business” should be set to Disabled
2. Delete all biometric sign-in information by running a command
certutil -deleteHelloContainer
I have not tested but the same might be achieved with commands
reg add HKLM\SOFTWARE\Policies\Microsoft\PassportForWork /v Enabled /t REG_DWORD /d 0 /f
certutil.exe -DeleteHelloContainer
Account protection and Indentity protection settings for computers groups takes a long time to get applied. Normalli those are not applied when first users try to sign in.
Having same problem. Can you site your source for where “Micrsoft confirmed that at the moment you cannot disble Windows Hello from Intune.”
We are not getting the prompt at OOBE, but at user first login, which is annoying as students don’t always get the same laptop so they either setup a pin on each device or quit the ‘need more information’ dialogue then get ‘something went wrong and they can skip for now. It then comes back at next login. Any thoughts on getting rid of that? We’ve disabled using the 3 methods above.
That’s surprising – if you block Hello for Business using the Windows enrollment settings, it shouldn’t come up for anyone…
And you’ve also deployed the Identity Protection Hello for Business setting?
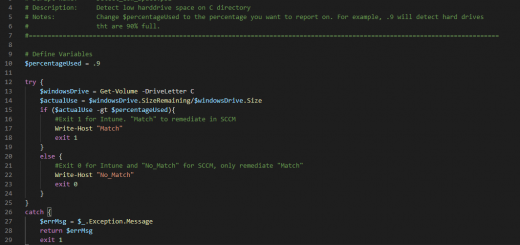
Hi, as Ed pointed out above there is a registry edit that will prevent the Windows Hello prompt from showing up during autopilot. If you’re using Intune you can deploy a power shell script to set this registry key automatically. This still allows the user to use Windows Hello if they like.
Here is what I use (can’t find original source to credit, sorry!):
$RegKeyPath = “HKLM:\SOFTWARE\Policies\Microsoft\PassportForWork”
$PassportEnabled = “Enabled”
$PassportPostLogon = “DisablePostLogonProvisioning”
$StatusOn = “1”
$StatusOff = “0”
if (!(Test-Path $RegKeyPath))
{
Write-Host “Creating registry path $($RegKeyPath).”
New-Item -Path $RegKeyPath -Force | Out-Null
}
#PassportEnabled: StatusOn = Windows Hello enabled, StatusOff = Windows Hello disabled
#PassportPostLogon: StatusOn = Windows Hello for Business prompts post Windows login, StatusOff = Windows Hello will prompt
New-ItemProperty -Path $RegKeyPath -Name $PassportPostLogon -Value $StatusOn -PropertyType DWORD -Force | Out-Null
New-ItemProperty -Path $RegKeyPath -Name $PassportEnabled -Value $StatusOn -PropertyType DWORD -Force | Out-Null
#Forces system to refresh
RUNDLL32.EXE USER32.DLL, UpdatePerUserSystemParameters 1, True
I am getting authentication issues.. with no access.. and error code 403. I believe it may have something to do with lacking an active school email account. Maybe I need to do a clean install for Windows 10/11 to remove education version?
A 403 error generally occurs when you don’t have access to a resource – so it may be that you don’t have rights to edit this setting or access MEM.
I am able to block windows hello but once i setup the autopilot device i get signed in and when i signn out i am not able to sign back in. My O365 environment is federated throught okta and not sure why i am not able to sign back into the device after signing out. Any ideas.
Unfortunately I’m not very familiar with okta federation. I did approve your comment in case anyone else would like to give recommendations.
I was able to fix this by setting up a sign on policy with okta Microsoft 365 app. Setup policy at the top of the policies and setup legacy and windows 10 and you can use basic auth to login to into the windows devices and this allows for password changes to be instant as well to be able to get back in.
Related question – Within endpoint manager, we have windows hello configured to “not configured” but are being prompted to window hello. I read the last part of your article which explains how this is to do with O365/Azure registration which makes sense. Where then is it configured? We have a complexity policy being applied that I’m trying to update but can’t find the setting/policy in either O365 or MEM.
Needs to be set to Disabled to prevent the prompt. Not configured will leave the default, which is prompting for hello setup.